Search This Blog
Wednesday, December 24, 2008
Tokyo Gore Police 東京残酷警察 Trailer
Monday, December 22, 2008
Live Messenger 2009 is out!
http://download.live.com/
Well, if you hate advertisements like me, you will probably want to "patch" your messenger with A-Patch:
http://apatch.org/downloads.php
Its a pity that mess.be is still far behind the patching. I like that better.
Tuesday, December 09, 2008
What I do for a living (The Good)
Monday, December 08, 2008
Free Legal version of IObits Advance SystemCare Pro V3
FREE IObit Advanced SystemCare PRO v3 License Key Codes Exclusive for Raymond.CC Readers
Thursday, November 27, 2008
Install Fedora 10 on Virtual PC 2007 SP1
Wednesday, November 26, 2008
Afterdark Horrorfest 3
- The Broken
- Slaughter
- Perkins 14
- Butterfly Effect : Revelation
- From Within
- Dying Breed
- Autopsy
- Voices
Publishing source codes onto Blogger
List to Range in Excel
Imagine we have this on the first column of an Excel sheet. What we want on the second column is:
1 3-4 6 8-10 14-15 19-20 22
Sound dead simple right? Ok, maybe you can skip reading this then. While its sound simple, it took me 15 minutes after a cup of 7-11 Slurpee Brainfreeze to write this :
Lets run through this a bit. I had added in as much comments as possible. Basically, you can play with 2 variables for your need.
- sRow which is which row to start making the range.
- col which is which column the result will appears.
For those who like insult to injury, to do this in Perl, its simply :
@a= (1,3,4,6,8,9,10,14,15,19,20,22);
Tuesday, November 25, 2008
Why RAID 5 stops working in 2009...
Monday, November 24, 2008
Pointsec Virus Protector
Corporate Windows Update
Windows Registry Editor Version 5.00
[-HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\LocalUser\Software\Microsoft\Windows\CurrentVersion\Policies\WindowsUpdate\DisableWindowsUpdateAccess]
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"NoWindowsUpdate"=dword:00000000
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"NoWindowsUpdate"=dword:00000000
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU]
"NoAutoUpdate"=dword:00000000
"AUOptions"=dword:00000000
[-HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
[-HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\WindowsUpdate]
[-HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"NoDevMgrUpdate"=dword:00000000
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main]
"NoUpdateCheck"=dword:00000000
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\WindowsUpdate]
"DisableWindowsUpdateAccess"=dword:00000000
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"NoWindowsUpdate"=dword:00000000
Save it and run it. Of course if you are hardcore enough, you can manually edit these registry. Make sure you make a backup in any case. There is also a file which is done up so you can download and run it from : Link
Well, happy updating.
Thursday, November 20, 2008
Truecrypt 6.1
Anyway, they got this right this time.
Download it at:
http://www.truecrypt.org/downloads.php
Wednesday, November 19, 2008
Pointsec Rootkit Protector
Basically, it applies to all the disk based encryption, more especially on those which cannot be reversed. But I decided to mention Pointsec because this is where I got it working. Most company will encrypt the whole disk especially in banks, military agencies.
Next, we have a concept rootkit, which should be fairly powerful to mask itself from all if not most conventional anti-malware. We can assume in a "perfect" environment where if the rootkit is loaded, it cannot be detected in the same environment. So as long as you have the OS running with the rootkit installed in Ring 0 layer, you are screwed so to speak.
Traditionally, in this case, we would attempt to remove or disable the malware by booting it up with an alternative environment such as WinPE or Linux. Then we can perform a scan on hte FAT/NTFS and wipe out the rootkit. Now, this is where it get tricky. Because disk based encryption is used, there is no way an alternative environment will be able to see the files on the infected Windows. So far I have only encounter Microsoft's Bitlocker which can be decrypted. And in this case, it is possible to remove the rootkit after decrypting it.
By now, I think you can figure out what I am trying to say. The only way to wipe out the rootkit is to destroy the whole encrypted partition. And as long as the partition is still encrypted (in my case using Pointsec), there is virtually no way to even read the partition using another OS. In a way, Pointsec protects the rootkit from being isolated and destroyed. That is in the first place if someone even figures out that there is a rootkit in place.
Where this can be applied? Well, almost everywhere where company can afford to have all their laptop encrypted and pay enough to acquire a really god rootkit. The company can effectively spy on their employee and perform logging or auditing services. And even if the employee finds out, there is nothing they can do. Well at least in countries where privacy is not protected by law.
Ok, I am not going to leave my contact here, but if you think your organization requires such a services, drop me a comment. :)
Microsoft to offer FREE Anti Malware in 2009 codename "Morro"
http://windowsonecare.spaces.live.com/
In short. Onecare will be discontinued in June 2009 for sale at least. By then, I would expect that Morro will be available in Beta. So, if you did not pay for Onecare, you won't need to for Morro either.
I cannot say how good this may be because it is likely Microsoft will strip off the additional functions such as tuneup, photo sharing, backup etc. So, it may be a give and take thing.
The only advice I can give for those who are facing expiry of their subscription soon: Renew of switch to a new Anti Malware first. Morro will be a while. If your expiry is far, go on with it and wait. By Spring 2009, I will expect a beta of Morro to be available.
Monday, November 17, 2008
D-link DIR-655 Firmware 1.21 with USB support
http://tech.slashdot.org/article.pl?sid=08/11/05/2220213&from=rss
The changes are as stated on their support page:
http://support.dlink.com/products/view.asp?productid=DIR%2D655
Anyway, what they did not tell you is that there is a official firmware 1.21 which does not contain the Secureport function and you can download it at:
ftp://ftp.dlink.com/Gateway/dir655/Firmware/dir655_firmware_121_no_securespot.zip
Saturday, November 15, 2008
Dawn of War 2
Thursday, November 13, 2008
Umi no Tririton 海のトリトン OP、ED
Wednesday, November 12, 2008
Factory Farming
Monday, November 03, 2008
YSMenu Oct 2008
YSMenu is basically japanese and to make the firmware and files for the NDS requires a hell lot of steps. You can read all about it at :
http://www.gbatemp.net/index.php?showtopic=97615
but I had save you some time by prepaing it and patching it with the DSTT firmware from :
http://www.gbatemp.net/index.php?showtopic=71613
And to make it all right, I added the cheat list as of 28 Oct 2008. In addition, I even throw in the GBA/GBC Emulator into the package.
So, with all these works put in, tell me why you will not download this for a shot on your NDS R4?
Grab it at:
YSMenu Oct 2008
PSP Slim 5.00 M33-3
BTW, you need 5.00 M33 in hte first place to perform this update.
Download 5.00 M33-3 here:
PSP 5.00 M33-3
PSP 5.00 M33 0xFFFFFFFF PSX Error Fix v2
1. Press and hold [Select]
2. Change the USB Device to Flash 0
3. Exit
Now activate the USB connection menu. Go to this new weird drive. If you cannot see "KB" folder, make sure you unhide system and hidden directory in your Windows. Now, extract the package you download here to the root of this drive. Safe remove the drive and exit USB menu.
Repeat the above steps, but set it back to Memory Stick. You have just flashed a file into the firmware and this patch is done.
Download the PSX fix for 5.00 M33:
PSP 5.00 M33 PSX Fix
Basically, just for the fun of it. I heard that Popsloader still does not work properly and PSx seems to be a big problem in 5.x firmware. So, if you are a hardcode PSX gamer on PSP, I would suggest skipping the whole 5.00 M33 until I say its good for PSX. :)
Lastly, why this is v2, apparently, v1 doesn't work so well.
PSP Slim 5.00 M33 Savestate Plugin
Download the PSP Slim 5.00 M33 Savestate plugin:
PSPS 5.00 M33 Savestate
P.S. I do not need to mention that this only works on firmware 5.00 M33, I hope.
PSP Slim 5.00 M33
Here is the Core firmware. The usual applies. Unpack it to the root of your memory card as all the directories has been created for you. DO NOT FORGET TO PRESS O TO REBOOT AT THE END OF THE FLASHING!!! Or you will brick you PSP as usual.
Download PSP 5.00 M33:
PSP 5.00 M33
Sunday, October 26, 2008
Hack in the Box 2008
For full details on what will be presented, check out the HITB website at :
http://conference.hitb.org/hitbsecconf2008kl/agenda.htm
Its pretty obvious I will be stuck in Track 2 because the first one from Track 1 is from Oracle. Of course, other reasons are the speakers from Track 2 are my usual favorites.
Anyway, if you are there at HITB, I hope I can meet you there for a chat. See ya there!
Microsoft Windows RPC Vulnerability KB9358644 MS08-067 (CVE-2008-4250)
Another reaon is probably not a good news. The bad guys beats us to it again as usual. There had been signs of attacks based on this exploits in the past 2 weeks and in fact now, there are 2 known trojans (info collector so far) which made use of this exploit. This exploit is serious enough for Microsoft to issue a special bulletin in their security software which reminds the user to update their machines in order to avoid infection.
So, can you please do this upgrade if you have not on 24 Oct 2008. You can download the files directly or use the normal Windows update to get this patch.
For a more detail FAQ :
http://blogs.securiteam.com/index.php/archives/1150
Sunday, October 19, 2008
科學小飛俠 ~ 日文版
科學小飛俠 ~ 台灣版
Tuesday, October 14, 2008
Russian Company manages to break WPA/WPA2 100 with GPU
Is this the beginning of the end? Even when 802.11n is still in draft, WPA2 is dead?
Read all about it :
http://securityandthe.net/2008/10/12/russian-researchers-achieve-100-fold-increase-in-wpa2-cracking-speed/
風暴 - TVB 少年四大名捕主題曲 完整版 ~ 林峯 吳卓羲 馬國明 陳鍵鋒

風暴 - TVB 少年四大名捕主題曲 完整版 ~ 林峯 吳卓羲 馬國明 陳鍵鋒
曲:鄧智偉、葉肇中 詞:鄭櫻綸
林 峰:
如若你不再逗留
我為了夢想的守候
曾為你心碎過後 長痛承受
吳卓羲:
如若你走盡頭 痛恨似在一生左右
如學會放低所有
無悔今後
馬國明:
風雨中 背叛裏似失控
當日我怎付出 才像惡夢
陳鍵鋒:
飄泊中 背負了有多重
情褪去才看懂
合 唱:
才相信
為何尋覓總可感到 渺無尺度
為何沉默只可能得到 烈變風暴
誰人曾被風急輕掃 也留記號
誰人來用心的擺佈
烈變風暴 再度
林 峰:
平靜各走各路途
蘊釀那未知的風暴
吳卓羲:
難避過創傷苦惱 悉緒的霧
馬國明:
風雨中 背叛裏似失控
當日我怎付出 才像惡夢
陳鍵鋒:
飄泊中 背負了有多重
情褪去才看懂
合 唱:
才相信
為何尋覓總可感到 渺無尺度
為何沉默只可能得到 烈變風暴
誰人曾被風急輕掃 也留記號
誰人來用心的擺佈
烈變風暴 再度
誰人曾被風急輕掃 也留記號
誰人來用心的擺佈
烈變風暴 再度
Tuesday, October 07, 2008
Slayers Revolution
And yes, the next season will be Slayers Glory!
Monday, October 06, 2008
Gundam 00 Season 2 Trailer
We are GUNDAM! We will destroy the rebirth!
Tuesday, September 30, 2008
Who killed Server Rabbit? Finale
Now, take a step back. So what? I still ahve admin running and it was not working when I log in as admin. The reason being even if you are admin, it does not mean all the services are run as admin. Some of them are still run as other roles and these role unfortunate to say happens to be one of the removed one!
My gut feeling this was the root cause. I checked with another working server / workstation and restored the deleted roles into one of the Server Rabbit and ta-da... Everything was working and kicking again. Actually as long as RPC service is up, I pretty much knew I hit it.
Well, here is the aftermath of the whole incident.
1. There are malware found. Incidentally, this means the malware protection is not enough. Even if this time the malware did not take it down, sometimes in the future, it will.
2. There was no backup. Having a good snapshot / backup will save the situation and minimize the downtime required to recover the whole problem.
3. There is not enough documentation. This applies to logging as well. If there logs and documents are properly put in place, the whole incident could had been easily tracked simply from the look of the documentations.
4. There is insufficent training. While its a good idea to have some of the admin learn how to harden or improve certain functions, it is always good to provide the admin sufficent training to do so. With proper training / certification, the admin would had avoided the incident.
5. Access control was not properly inplemented. The sharing of accounts had made the whole investigation a nightmare. If individual accounts were used, combined with properly logging, it would had provided the information who made some change at what time. This could had greatly help the investigation.
6. Logging is the last time that I felt was missing. In terms of the firewall, IDS etc. If proper logs were generated, I would had concluded whether this was a security incident or not from the very start based on who has accessed the server etc. Of course lets not forget the golden rule that if a machine is compromized, the log is as good as none. Therefore logs from hardware boxes (which is probably not the target of the attack) is greatly helpful in determining whether a real intrusion has taken place or was it simply a misconfigureation or software corruption.
I am glad this was not my day in day out job. :) Well if it is, I am hell not getting paid enough for this. :)
Thursday, September 25, 2008
Samsung Omnia / Orca Firmware HH3
What are you waiting for? Grab it at :
http://www.samsungmobile.com/promotion/omnia/sg/sub02_Vista.jsp
CWCheat 0.22D
Here is the download :
http://rapidshare.com/files/148169481/CWCheat22D.zip
Sunday, September 21, 2008
Yet another 8 films to die for
http://www.horrorfestonline.com/
Highly recommended for horror fans!
Friday, September 19, 2008
Who Killed Server Rabbit? Part 4
Who killed Server Rabbit? Part 3
Who killed Server Rabbit? Part 2
Who killed Server Rabbit? Part 1
Good riddance to bad rubbish ~ SingTel
Tuesday, September 16, 2008
Microsoft Dot Net Framework 1.1 SP1 for Vista
There is a page that will show you how to extract the files and patch it before installation here:
http://kbase.gfi.com/showarticle.asp?id=KBID003100
Well, you do not need to do that anymore. I had decided to slipstream the whole package so that it can be installed directly on Windows Vista.
Simply download the package below, extract all of it. Then just run netfx.msi.
http://rapidshare.com/files/145885903/dotnet.zip
Monday, September 08, 2008
Beware of the SingTel Shop scam!
Guess what? They already charged to my credit card! I called and they insist they will not honor the purchase and will not send the phone to me.
Tell me if this is not a scam, what is?
I strongly advise anyone to think again if you are really buying from singtelshop.com. Or in the first place, does SingTelShop even belongs to SingTel? they have such differences in prices. For all you know, this is a phishing site!!!
Anyway, I am going to call my credit card company to cancel the purchase.
Singtel fcuks up again!
To singtel :
I had placed an order 100****** online because I wish to avoid the queue at the shop. I had followed all the intruction, scanned the student pass for the student line etc, However, next working day I got a call to say the order is cancelled!!!I was told that ST cannot honor the signup done online and I had to do it at the Hello Shop? WTF? Then why have Singtelshop.com at all? It even wasted mt time to scan and upload the image!
Then I checked at the HelloShop... The price of the handphone is doubled!!! Why do you published price which you cannot honor at all? You had totally wasted my time and my opportunity to sign up with SH or M1!!! If you so desire to do so, you might as well put all your phone at $1 on Singtelshop.com since you cant honor the pricing anyway!
Sunday, September 07, 2008
Goodbye Xiao P

Xiao P has past away on 2nd September after he was with me for over 2 years. I would estimate he lived about 2 yrs 3 months at least which is already far longer than an average pudding. He was still ok 2 night before when I played with him in his playground and I gave him a lot of his favorite food. He was still digging through them playfully.
Then the night before I saw him lying down weird. I knew the day was finally coming. After giving him some honey water, he seems better and he seems to do his very best to run around just to show me he is ok. What makes the whole thing even more sad... I comforted him and transfer him to somewhere quiet. Then after a while he slept peacfully and quietly. I couldn't sleep that night.
At about 5am I woke up and he was still and starts to harden. I did what I had to and give him a proper buiral.
I will alwasy miss you Xiao P. I have to stop here...
Facebook DoS PoC
http://www.facebook.com/apps/application.php?id=8752912084
demostrated a PoC of how Facebook can DoS another site. This app basically in short show 1 photos from National Geographic. But downloads 3 more huge files from somewhere else. Or for that matters, you can do upload, posts, requests or whatever you can imagine using hte Facebook API. Effectively, all you need is millions of people to sign up your app, then when they log in, they become your botnet to DoS someone.
For example, I can up my site counter to millions easily by creating a bogus app that gives free paypal money when you refer someone. Of course on the side line, I can con some paypal accounts as well. :) Then I can make a hidden read to my site in the app and not disaply it. Once millions sign up, millions will visit my site. OK, shake this off your head. This is a (C)Copyright idea... Hahaha. Seriously, its that simple. Make you wonder why it hasn't happen yet. (Or is has... We just did not hear of it)
Anyway, here is the full whitepaper :
http://blogs.zdnet.com/security/images/facebotisc08.pdf
Google Chrome Updates to v0.2.149.29
The good thing is Google is putting this in spotlight and fixing as we move along. Of course, thanks to the millions of Beta testers like you and me who is trying so hard to 0 days this. I guess I will work on something else now...
IE8? Maybe...
Wednesday, September 03, 2008
Google Chrome - Zero Day Buffer Overflow
BTW, Google Chrome can be downloaded via :
http://www.google.com/chrome
After installing, just type this into the URL :
xiaop:%
or if you are lazy, browse to Crash Chrome
Yes, immediately, Google super friendly error message will greet you :
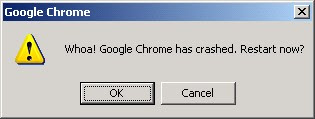
Well, if you had installed the right stuff, you can kinda find out what happen :


Of course, this is a buffer overflow.
Well, if this doesn't worry you about the way Google release this software, take a look at this :

This won't look too good if you had been surfing content rich multimedia sites (which Chrome is optimized for) such as Playboy or something...
Sunday, August 24, 2008
Get your free 120 days Windows Home Server Trial now
http://www.microsoft.com/windows/products/winfamily/windowshomeserver/countries.mspx
Saturday, August 23, 2008
Enabling Hibernation in Windows Vista
First, you have to ensure its not already on. Look for the file Hiberfil.sys. If you use the Disk Cleanup function, sometimes this file is delete and Hibernation, as a result, is turned off.
If the file is missing, do this :
1. Click Start, and then type cmd in the Start Search box.
2. In the search results list, right-click Command Prompt, and then click Run as Administrator.
3. When you are prompted by User Account Control, click Continue.
4. At the command prompt, type powercfg.exe /hibernate off, and then press ENTER. Actually I found that powercfg /h on will work too.
5. Type dir c:\hiberfil.sys. You should see the file now.
5. Type exit, and then press ENTER.
Then, obviously, if you want to turn it off, replace the on with the off.
Now, the next step is that if you have not reboot, the hibernation function is not yet enabled on you shutdown menu in Vista. And if you are stuck with a damn long process which can be paused, but cannot be resumed if you restart.. then its time to force a hibernation immediately.
To do that :
1. Click Start, and then type cmd in the Start Search box.
2. In the search results list, right-click Command Prompt, and then click Run as Administrator. Note that it may or may not need administrator rights to hibernate the computer.
3. When you are prompted by User Account Control, click Continue.
4. At the command prompt, type shutdown.exe /h, and then press .
Oh, you have pressed. There it goes. If for any chance you want to abort the shutdown, just execute shutdown.exe /a. This is a damn good way to do debugging for the RPC worm if you remember.
Thursday, August 21, 2008
Gundam 00 Season 2
http://www.sunrise-anime.jp/news/gundam00/
I am quite anticipating the season and really looking forward to see how the story will unfold. But (SPOILER) one thing is for sure, all the C.B. pilots survived. Its just 1 plus month away.
Tuesday, August 19, 2008
Creative use of CVE-2008-2281 and Evilgrade Demo
Here is the demo I mentioned a while back but have not gotten the time to upload it. I had split the demo into 2 sections. Like how a magician does it. The first one here you will see what will happen, but not how it is done. In another post later, I will show you how it is done and why this is happening.
Sunday, August 17, 2008
任潔玲 ~ 我們有沒有愛過
I remember losing sleep in camp during the night waiting for this MTV to come on and its usually the last one cos its No 1 on the charts. Well, its still a classic.
大海 ~ 张雨生
This is the original by 张雨生. I am sure we miss his voice. This is one song I will not attempt so that I can keep a good memory of it. And, btw, I can't unless its down a few octave... :P
大海 ~ 楊培安
从那遥远海边慢慢消失的你
本来模糊的脸竟然渐渐清晰
想要说些什麽又不知从何说起
只有把它放在心底
茫然走在海边看那潮来潮去
徒劳无功想把每朵浪花记清
想要说声爱你却被吹散在风里
猛然回头你在那里
如果大海能够唤回曾经的爱
就让我用一生等待
如果深情往事你已不再留恋
就让它随风飘远
如果大海能够带走我的哀愁
就像带走每条河流
所有受过的伤
所有流过的泪
我的爱
请全部带走
This song was one of my favorite originally by the late 张雨生. I am happy to see that 楊培安 has sang it very well indeed. This song does bring back memory of a story at a certain seaside on a rainy night...
三国志全日本超级动画主题 《风姿花传》~ 谷村新司
風は叫ぶ人の世の哀しみを
星に抱かれた静寂の中で
胸を開けば燃ゆる 血潮の赫は
共に混ざりて大いなる流れに
人は夢見る ゆえにはかなく
人は夢見る ゆえに生きるもの
嗚呼 嗚呼 誰も知らない
嗚呼 嗚呼 明日散る花さえも
固い契り爛漫の花の下
月を飲み千す宴の
君は歸らず殘されて伫めば
肩にあの子の誓いの花吹雪
人は信じて そして破れて
人は信じて そして生きるもの
嗚呼 嗚呼 誰も知らない
嗚呼 嗚呼 明日散る花さえも
国は破れて 城も破れて
草き枯れても 風は鳴き渡る
嗚呼 嗚呼 誰も知らない
嗚呼 嗚呼 風のその姿を
嗚呼 嗚呼 花が傳える
嗚呼 嗚呼 風のその姿を
风呜咽,低诉人间愁怨;
夜寂静,怀揽繁星满天;
心胸开,热血有如烈焰;激流汇,化作洪流闪电。
梦中人,渐已入梦;梦中梦,人生如梦;
呜呼 呜呼 谁人知晓?呜呼 呜呼 明朝花落多少?
花烂漫,见证无悔誓言;共举杯,同饮月影一片;
望君还,孤独伫立此间;花已残,化雪轻洒我肩。
人有信,而言无信;有信人,为信而生;
呜呼 呜呼 谁人知晓?呜呼 呜呼 明朝花落多少?
国已破,城亦陷,枯草黄,风呜咽。
呜呼 呜呼 谁人知晓?呜呼 呜呼 风姿如此窈窕。
呜呼 呜呼且问飞花。呜呼 呜呼 风姿如此窈窕…
Saturday, August 09, 2008
Tuesday, August 05, 2008
Disgaea - Afternoon of Darkness End Save
This package includes all 9 endings (Etna Story ending as well). Just unpack them and read the DOAD.txt in the main directory and put the rest into your PSP where saves are.
Hope this help you see all the ending without having to go through what I had done for you. Please leave me a comment here when you download ok?
Disgaea End save :
http://rapidshare.com/files/134899145/Disgaea.rar
Friday, August 01, 2008
Creative use of CVE-2008-2281 and Evilgrade
Well, what I am going to demo here is not state-of-the-arts and neither it is 0-day. Well, at least the vulnerability is not 0-day, but the way to make use of this sure is... :) CVE-2008-2281 is just a less critical or low vulnerability. But combine with the newly release Evilgrade (well, I could had done it with my own web server too, but why waste time on things that others had already done up for you?).
A bit of background on the 2 things I will use here. CVE-2008-2281 is referred to as the Print Table of Links vulnerability. I will put up some links about this at the end of this. But in short, this affect you when you print using IE6,7,8 (beta for now) and under options, select "Print Table of Links". By far, only librarian uses them as far as I know.
The second thing I use is call Evilgrade. In short Evil upgrade. It can emulate upgrade servers of popular software from Java, Winzip to many others. Windows Updates is not possible due to the signing of the package. (For Now). So I guess you already know what I am going to do...
Well, keep guessing. But I will release my video soon as soon as I get the recording working.
Monday, July 28, 2008
Secure Computing Sidewinder vulnerable to DNS Query Port Weakness
No, seriously. You should patch this and this is a serious problem. This is related to the famous DNS poison exploit that is running wild with is tagged with CVE-2008-1447. It affects both Sidewinder and Sidewinder G2.
So, go patch it before someone "patches" your DNS for you.
P.S. Working codes is out for BIND 9.x and Metasploit framework. Go play with it now.
Wednesday, July 23, 2008
Windows Home Server Power Pack 1 RTM
The other improvements includes backup enhancements including the ability to backup to USB connect drive, backup your WHS share folders. Of course, the power consumption has been fixed to give it a more green environment friendly feel.
Download WHS PP1 from :
http://www.microsoft.com/downloads/details.aspx?FamilyId=1A6AEF46-DB57-401F-814F-6EFA26E7A1E8&displaylang=en
Put that onto your WHS onto the software directory. Remote desktop into it and launch the installer. After that you will need to go onto each of your client machine and follow the instruction to upgrade the client connector software. Its goes something like http://
My advice is to immediately launch the connector software and perform a backup. Why? If you do so, you will released your security suite will detect the connector software has changed and it will prompt you for allow/deny the backup engine. Imagine if you have not done so and leave it overnight hoping it would somehow worked, well it won't. You will have to allow it and save the config this once. Well, if you have no such issue, I suggest STRONGLY that you get a client side security software. I am using Microsoft OneCare which has report it doesn't play nice with WHS. It worked for me anyway now that I am on OneCare 2.5 anyway.
Friday, July 18, 2008
Keeping the rows together in MS Word
Ok, if you understand the problem, then I am happy to tell you, after wasting 5 minutes on it and many click and check on google and whatever, I finally found the solution!
There are a few problems :
1. Check your page setup, make sure its align to the top, not center, bottom or whatever. This is the most stupid part of it.
2. Ok, as suggest, uncheck allow rows to split across pages.
3. Select the table. Format->Paragraph. Line and Page Breaks tab. Uncheck "keep with next" and "keep lines together".
Now, it does get solved? I hope so. Mine did. Make sure for (3) you select the table.
Sunday, July 13, 2008
Tin of Paint ~ A Cyanide and Happiness Short
Cyanide & Happiness @ Explosm.net
Well you heard of Cyanide & Happiness. If you haven't, then you hear this from me. You like South Park and can take that extend of joke, you won't be disappointed. Visit and see daily comics and more shorts from explosm.net.
Microsoft OneCare 2.5 Released
To do a manual update, which is not advisible, you will need to uninstall OneCare first. Then go download it again and reinstall. Some of your settings and firewalls rules will be lost as a result. Well, if this is the way you choose, you can start from here :
http://onecare.live.com/standard/en-us/purchase/trial.htm?sc_cid=wlsc_centers&redir=true
True Crypt 6.0 Portable
True Crypt supports disk based encryption too. However, that would means that the host system needs to have True Crypt before it can open your encrypted disk. I would prefer another way to install that. Instead, you should download True Crypt and expands all the files into a folder or the root directory. Then create a file based encryption with the remaining space. In this way, you will be able to mount your encrypted file with the True Crypt binaries in the main directory on any machines. So, make sure you get all the version of True Crypt. For mac and linux as well if you want to mount the file there. You can also upgrade true Crypt easily this way. This give you truly independent OS portability especially on your PenDrive and Portable HDD. Unfortunately, its easier said than done. I probably wont go make a mac + linux binaries anyway, since they vaires so much.
Now, lets talk about the failing of this. True Crypt can fail in some ways. For example, you forget to eject the thumbdrive and pull it out. Or if you crashed Windows with a blue screen halfway writing to the Thumbdrive. Or the Thumbdrive simply goes dead. One solution for all 3. Backup. You can backup the raw or the encrypted file itself. Of course, there are ways to avoid issues especially from the first case. When you mount the file in True Crypt, choose the mount options and check mount volume as removable media. The 2nd and 3rd case is a bit hard to avoid, but do you know that there is rescue disk for True Crypt. This only applies if you encrypt the system partition though. Mount you file for the first time, select system->create rescue disk and follow the instruction. That proves to be a life saver sometimes in the 2nd and 3rd case. But in the case of a removable drive for True Crypt, this does not apply at all.
Well. The autorun.inf you will need to make the automount and dismount for hte thumdrive is as follows :
[autorun]
label=TrueCrypt
icon=truecrypt.exe
action=Mount TrueCrypt Volume
open=truecrypt /v
shell=mounttc
shell\mounttc=&Mount
shell\mounttc\command=truecrypt /v
shell=dismounttc
shell\dismounttc=&Dismount
shell\dismounttc\command=truecrypt /d
shell=runtc
shell\runtc=Run &TrueCrypt
shell\runtc\command=truecrypt
Just copy and paste the above into notepad and you need to edit
That was the old days way fo doing it. Now, just install and run Tools->Travellers Disk Setup and you will be guided with a wizard to creating the above. That takes all the fun away does it not...
Thursday, July 10, 2008
The Pentester's Art of War Chapter 0
First, lets take a look at the title of this article. Pentester. Well, I am sure it's a familiar term to many. A Pentester is basically a short of a Penetration Tester. Usually he is a security professional who conduct testing of the security of a subject (be it a application, network or even a physical location) by means of attacking it. Some people may want to use the word "hacking". I absolutely agree. However, there are many among the security professional who prefers not to be associated with the word hacking as it usually has a bad annotation.
I am sure some of you had already notice I used the word "he". Its not that I am male chauvinistic about this. I do admit there are a few pretty good security professional who are female. I knew a few from mother Russia. However, to make things simple, I would use the word "he" throughout. Just remember it can mean either sexes.
Next, the term "Art of War". The first reaction will be relating this to Sun Tzu's "Art of War". Well, I admit, I may be using something similar to run through these topics, but by no means do I want to translate it into a guide for Pentesters or explaining the whole book of Art of War. I remember there was somebody who would disagree with my term "Art". Pentesting is a science he would argued. I disagree. If Pentesting is a science, then simply it means that given the same application, for example, two different individual would have done the pentesting similarly (and maybe even word for word) and produced a similar report. If this is pentesting, no wonder my friend laugh at the joke about getting monkeys to do our pentesting in the future. I argued from the point that its an art because no two pentester will do it the same way. One might decided to deploy an sniffing attack on the application while another simply may want to unassemble some of the binaries. There are many ways and often the results varies. And I believe this is what makes one pentester better than another. I know this will hurt people who runs automatic tools such as nessus or appscan and then pull the beautiful report off their color laser printer and pass it to their boss. Sorry, strictly, I do not classify these people as pentester.
The term "War" probably raise some eyebrow. A serious Pentester treats his every project like a battle. In my opinion anyway. Each penetration test will have to be treated seriously like a war. All the strategy, the tactics to deploy as well as the resources gathering. All these plays a part in whether the project is successful or not. Of course, by means of sucessful, it means the Pentester found serious vulnerability and gotten in. Of course, the condition of winning will depends on each different engagement.
So, the following articles will concentrate on the strategy, tactics and the art of winning the war of pentesting.
Tuesday, July 08, 2008
Astalavista Security Toolbox DVD 2008 V5.0
Astalavista's Security Toolbox DVD 2008 (v5.0) is considered to be the largest and most comprehensive Information Security archive. As always we are committed to provide you with a resource for all of your security and hacking interests, in an interactive way! The Information found on the Security Toolbox DVD has been carefully selected, so that you will only browse through quality information and tools. No matter if you are a computer enthusiast, a computer geek, a newbie looking for information on "how to hack", or an IT Security professional looking for quality and up to date information for offline use or just for convenience, we are sure that you will be satisfied, even delighted by the DVD!
Let me just say that I am not advertising for this product and in my opinion, most people should not need this product at all, especially some of the security professional who would not like to be associated with words like hackers, blackhat etc. The tools inside this DVD is pretty blackhat if you ask me. There are tons of exploit codes and source for you to see and play around with (your VM that is). If you are hardcore enough, this is a great buy especially at this rock bottom price.
Read more from :
http://astalavista.com/index.php?page=340
萧十一郎 ~ 罗文 TVB 1978
历遍江湖千般凶险
捱尽世途困苦片段
自觉目光似剑 此心昭日月
情共爱 在脑海 尽化烟
梦里芳踪渺渺 怕触爱火烈焰
挥刀断水水更现
蜜意若灰寸寸 爱海有千叠浪
心头若絮乱
世间多情偏偏多怨
情路爱途已感厌倦
独对落英片片 顾影空寂寞
怀旧侣 忆往事 恨肠断
Saturday, July 05, 2008
PSP 4.01M33 Save State
Here is the download :
http://rapidshare.com/files/127353321/401M33-Savestate.rar
Remember you need at least 4.01M33 to operate this plugin.
PSP 4.01M33-2 Released
I had made everything simple this time. Just download the 4.01M33 package. Unpack the files into the root of your memory stick. Yes, I had created all the directories to make life simple. Run the updater. Follow all instruction. Again, let me stress that you MUST PRESS O when told to do so to reboot at the end. Do not power off or do something otherwise.
Download 4.01M33 :
http://rapidshare.com/files/127352946/PSP401M33.RAR
After that, download the 4.01M33-2 below. Just copy all to the main directory of your PSP memory stick again. Run the update. It will auto reboot and tada, you have 4.01M33-2.
Download 4.01M33-2 :
http://rapidshare.com/files/127353130/401M33-2.RAR
CWCheat 0.22 Rev C
Also, if you had others plugins installed, please do not copy all the files in step 1. Edit your pops.txt, game150.txt and game.txt to include the lines in these file. Its kinda like merging them into your current files.
Here is what you need to do (good for newbies) ...
1. Copy the folders into your memory stick main folder. All the directory has been prepared for you. See above if you have other plugins installed, do not overwrite your pops.txt, game150.txt and game.txt.
2. Power up your psp while pressing R
3. Select plugins
4. Press X over cwcheatpops.prx [POPS] it will say ENABLED
5. Press X over cwcheat.prx [GAME] it will say ENABLED
6. Press X over cwcheat.prx [GAME150] it will say ENABLED
7. Exit recovery
8. When in game press select for x3 seconds to access the menu(default options which can be changed)
Here is the download :
http://rapidshare.com/files/127354421/CWCheat022C.rar
Thursday, July 03, 2008
Back|Track 3 Release
In any case, here is the direct link :
Description: CD Image
Name:: bt3-final.iso
Size: 695 MB
MD5: f79cbfbcd25147df32f5f6dfa287c2d9
SHA1: 471f0e41931366517ea8bffe910fb09a815e42c7
Download: Click here
Description: USB Version (Extended)
Name:: bt3final_usb.iso
Size: 784 MB
MD5: 5d27c768e9c2fef61bbc208c78dadf22
SHA1: 3aceedea0e8e70fff2e7f7a7f3039704014e980f
Download: Click here
Description: VMware Image
Name: BACKTRACK3_VMWare.rar
Size: 689 MB
MD5: 94212d3c24cf439644f158d90094ed6a
SHA1: 21c9a3f9658133efff259adbe290723583b4fd82
Download: Click here
Yes, I know. It still doesn't play nice with Virtual PC. And BT3 , in my opinion, is really slow compare to BT2... You probably need to install Nessus 3 on this too...
Thawte Free Email Certificate vs Vista IE7
Well for those who did not know what a email certificate is... Imagine SSL.. Ok, even more plain, the padlock you will see on the browser when you do you internet banking... Well, thats encryption. SSL is basically encryption. But you need a SSL certificate to do the encryption. Email certificate is somethign very similar. But on top of being able to do encryption, email certificate also allow you to identify yourself. This mean when you friend / client receive a email signed by your email certificate, they can be sure its you. If the email ash been tampered, changed, edited, forwards etc.. the signing will fail and you will see a X on your email client. What? You are still using Lotus Notes? Man, get a real email client, FCS!
Anyway, back to this issue of using Thawte Email Certificates. Its FREE. Thats one plus point. And so far I tried many, like komodo etc.. And evne one which I will not name, who issue email cert, but their own SSL cert is kinda expired or blacklist... This is the type of CA you should avoid. In any case, Thawte has the advantage.
Sometime back in Dec 2007, thawte posted a "solution" to the Vista IE7 problem.
https://search.thawte.com/support/ssl-digital-certificates/index?page=content&id=S:SO5558&actp=search&searchid=1215093218617
Well if you do not know whats the problem, it can only means you are not using Vista or are using IE7 or below on XP. anyway, the problem is there is no support for creating the private key to make the certificate.
Anyway, if you follow the instruction above, you will hit the Error: "424 Object required" error.
Thawte suggest your try :
https://search.thawte.com/support/ssl-digital-certificates/index?page=content&id=SO5657
OK, stop right here. This is the step I strong advice you DO NOT do. Whats is the point of using a certificate when you have to cripple your security on your browser to get the certificate in the first place?
This is my approach :
Grab a machine with Win XP. Yes, a VM is good. Always keep Win XP VM around.
Go through the process and request the cert, then complete it by installing the cert.
Now, you will have to export the cert.
Ok, this is the tricky part. Listen carefully, or you will find that you cant import your cert properly later...
YOU NEED TO EXPORT YOUR PRIVATE KEY.
Choose that... then the rest you can play around with... use a good password. But I strongly suggest after importing sucessfully onto your Vista that you delete the exported keys away.
Put all your *.PFX together and bring it to your Vista machine. Open IE options and then import them. Just let IE decide where to put the certs. It should end up in the Personnel folder. Otherwise, you done it wrongly. See the CAPITAL above. Once all yoru cert if done, go ahead and sign some email with your Outlook and smile.
I try to be brief here cos I figure most of us knows what we are doing. If you have problem wit hthis instruction, please post a comment and I will try to help you out. For Firefox, the procedure is different, so lets just worry about IE / Vista here.
I wonder why I searched and cannot find this solution on Google...